ABAC Overview
Attribute-Based Access Control
The main idea behing Atttribute-based Access Control (ABAC) is to consider a request as a set of pairs (attribute name,attribute value), instead of a triple (subject, object, access mode). Hence, instead of relying on external information to be associated with the subject and objects (such as the access matrix, the BLP lattice, the Chinese Wall conflict of interest classes, or a set of roles), we now consider that all relevant information is provided directly in a unified format in the request. This request is then evaluated against a set of policies, which consist of structured sets of rules, and a decision is returned.
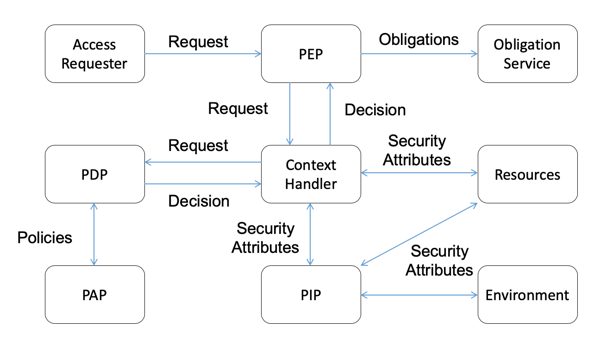
Access Control worklow as defined by XACML.
The overall worklow for a request is described above:
- The access requester submits a request to the Policy Enforcement Point (PEP), typically containing only the basic attributes (subject, object, mode)
- The PEP forwards this request to the Context Handler
- The Context Handler gathers all relevant attributes directly from the resources or from Policy Information Points (PIP), which collect information from the environment.
- The context Handers forwards the full request to the Policy Decision Point (PDP)
- The PDP retrieves the relevant policies from the Policy Administration Point (PAP), evaluates the request against the policies, and returns a decision (such as Permit or Deny) to the Context Handler.
- The Context Handler informs the PEP about the decision.
- The PEP either allows or rejects the request.
- In some cases, the PEP might have to follow-up on some obligations (e.g., delete some files after the request has been done, or inform another entity about the request), but we do not consider those here.
In the next section, we look at how to define rules, which are the basic components of an ABAC policy.